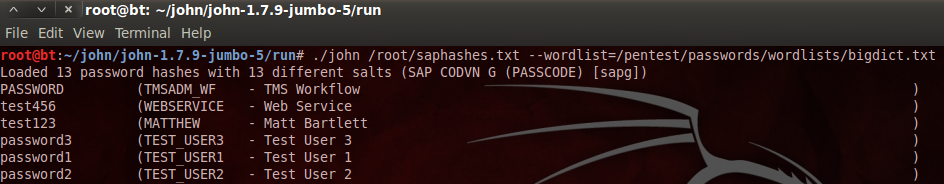
We’ve all been there and suddenly you need to add another developer to your Cloud Connector but alas you can’t remember your username and/or password.
Here is a quick way to find the username and reset the password.
These details are contained within the users.xml file and in order to find its location load up services from control panel or search for services.msc
Find the SAP Cloud Connector and double click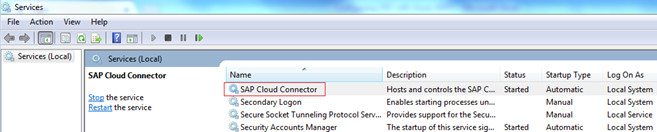 Note in my example the folder is c:\SAP\scc20\
Note in my example the folder is c:\SAP\scc20\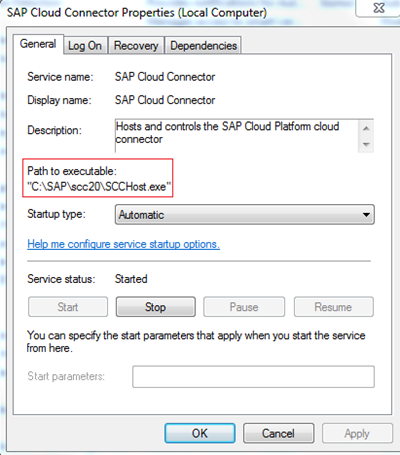
Open up Windows Explorer and browse to the folder and you should see the following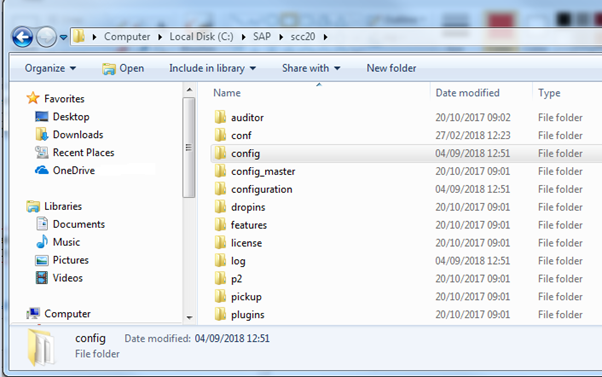
Look inside the config folder and open the users.xml file with notepad.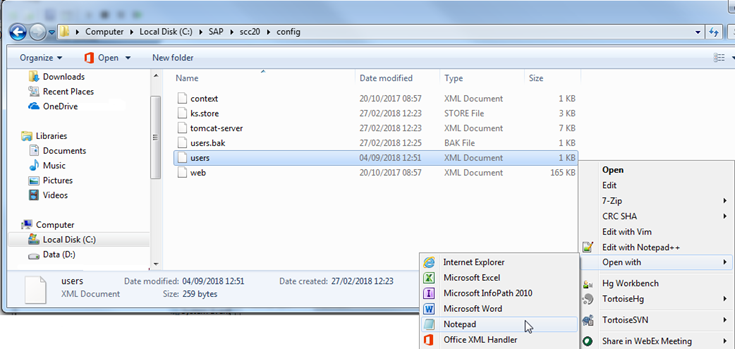
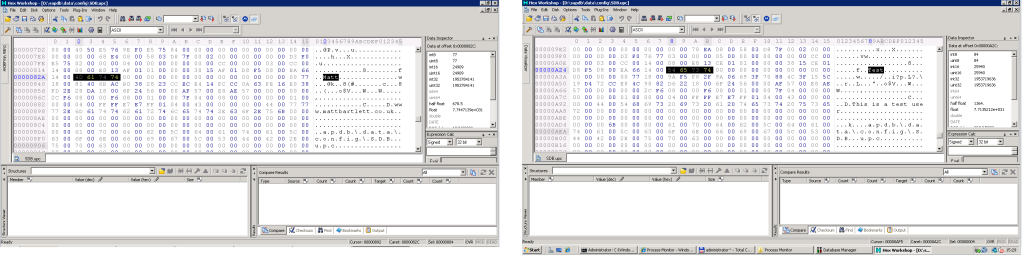
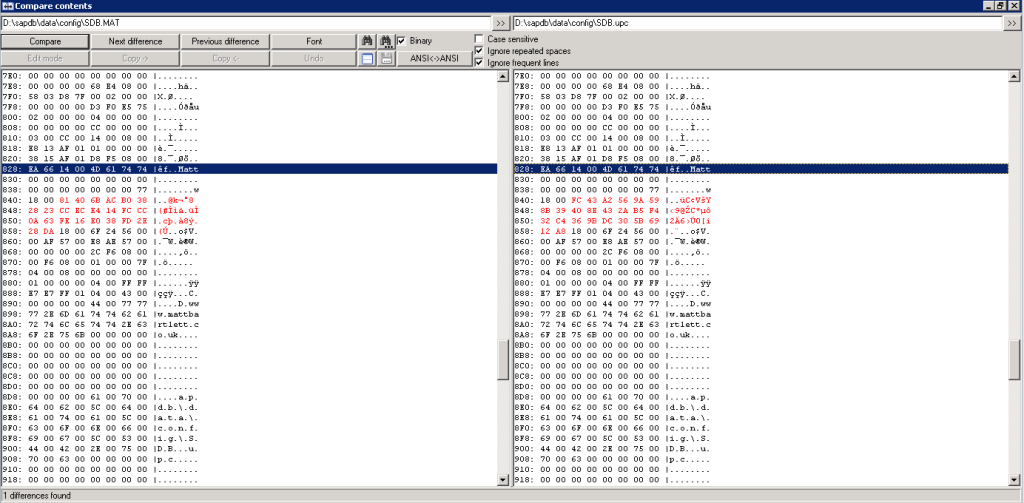
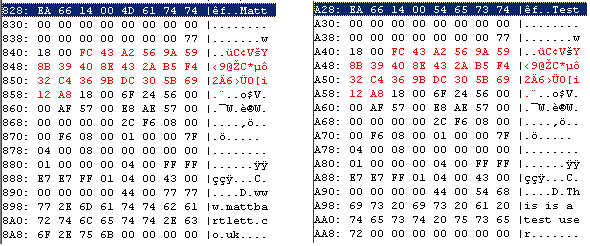
Here all users are displayed – note in my example users are Administrator and Matt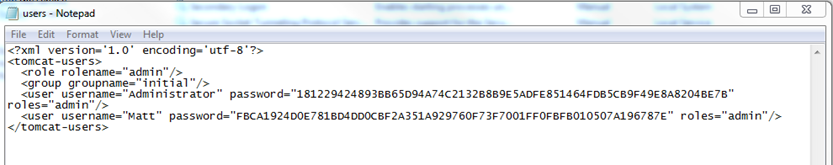
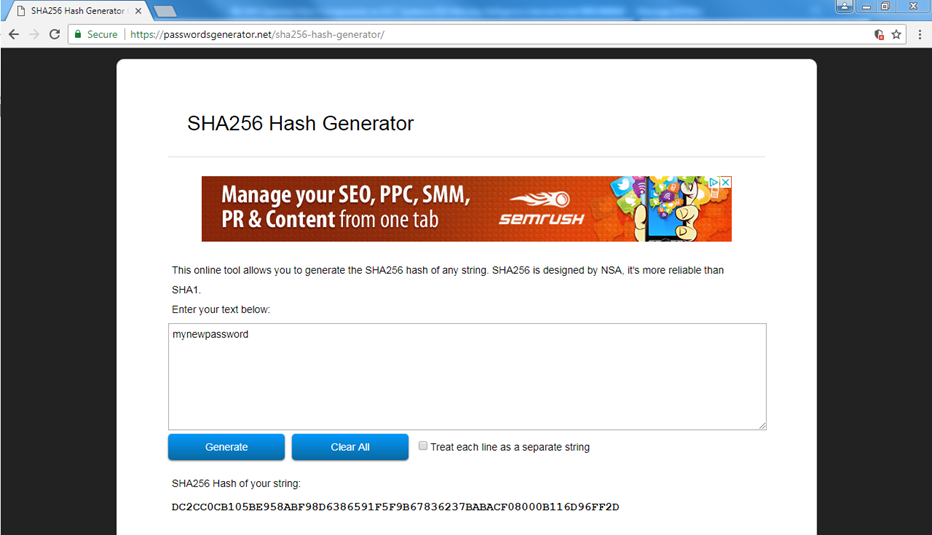
If I want to reset the password these are in SHA256 format – you can simply generate one using a website such as https://passwordsgenerator.net/sha256-hash-generator/
Copy the hash and paste into the users.xml file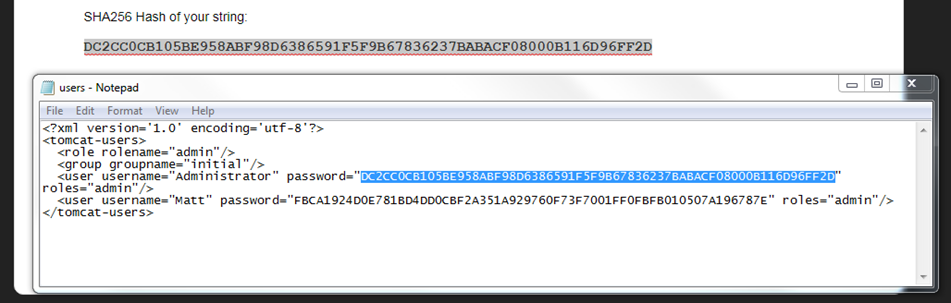
Save the file and restart the service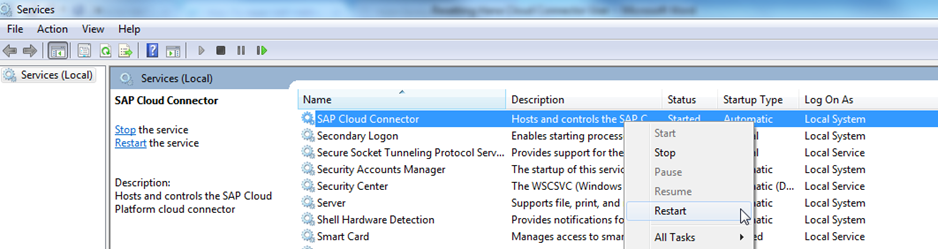
Now I can login with Administrator and a password of mynewpassword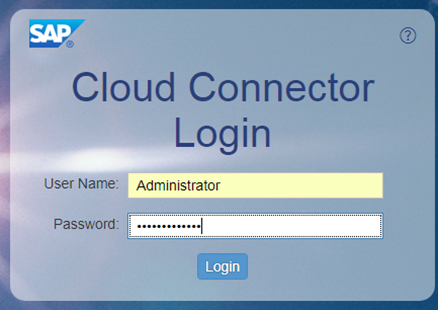
Some sample hashes for reference
password = 5E884898DA28047151D0E56F8DC6292773603D0D6AABBDD62A11EF721D1542D8
manage = 181229424893BB65D94A74C2132B8B9E5ADFE851464FDB5CB9F49E8A8204BE7B
For more information on configuring and installing the Hana Cloud Connector I can recommend this book: