Step 1: I fired up an excellent tool Process Monitor from SysInternals (Now Microsoft owned), opened up the database manager tool and reset my users password. I then reviewed all the events that had just happened, initially looking to see what files has been read from thus attempting to gain clues to how the change password operation might be working. Then later looking at what files had been written to ultimately hoping to see where the password might be saved.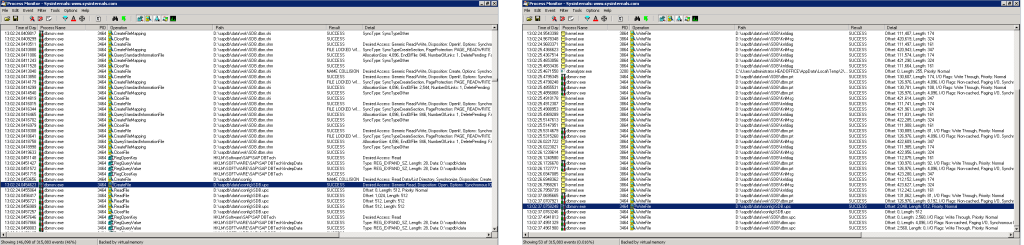
Step 2: From analysis of the sdb.upc file I could see my users in plain text. I could be on to something interesting. 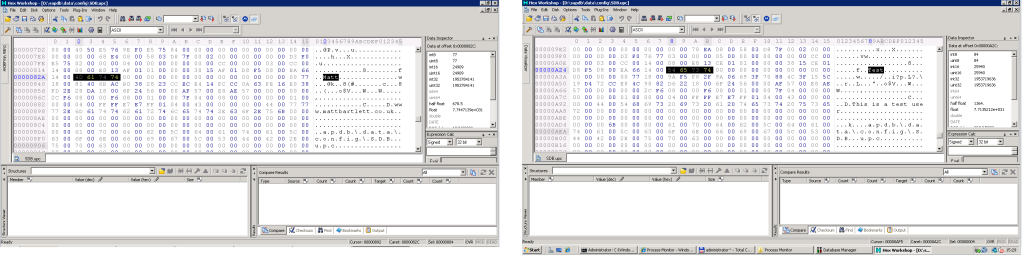
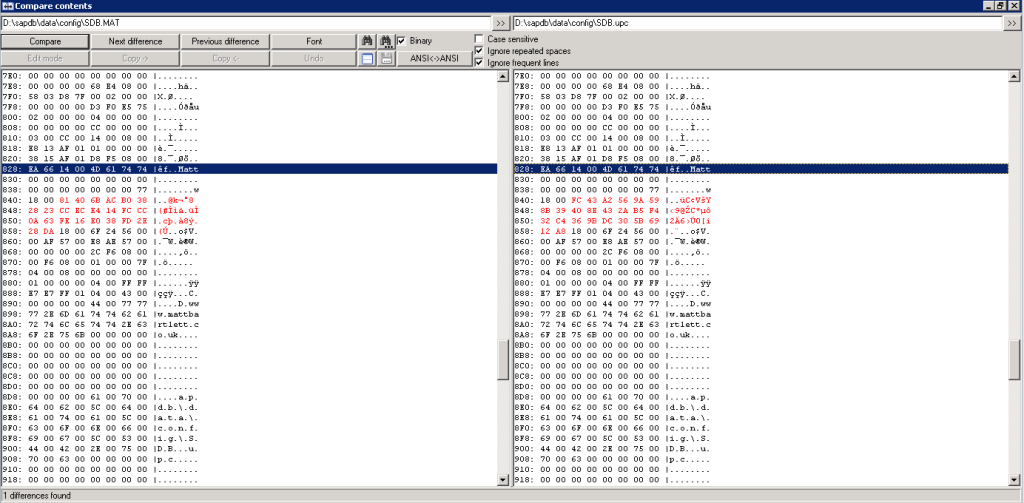
Step 3: After taking a backup of the upc file I changed the password once more and compared the two files. I could see clearly the only change made, this must be an encrypted version of the password.
Step 4: Now I was interested in see if the password was being salted with perhaps with a user name, hostname or some other secret. Comparing the password hashes across different servers, different versions and different database names showed no difference at all. Handy… for us.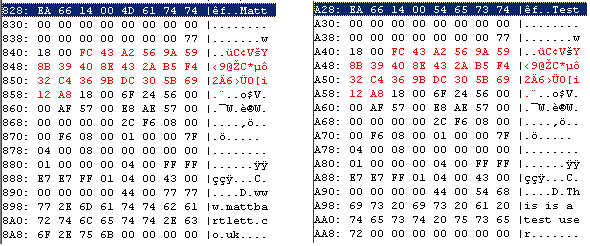
A quick check proves I can simply copy and paste hashes between password files to reset them. I tried simply setting the password hash to all zeros which works nicely but only for version 7.6 as later versions generate an error.